
A quick way to get HTTPS ingress into a Kubernetes cluster is to deploy the cloudlared container as a deployment or sidecar.
Follow the instructions for setting up cloudflared on your local machine.
1. Certificate Generation
So that cloudflared can authenticate itself when running inside your cluster we need to generate a certificate.
https://dash.cloudflare.com/argotunnel?callback=httpsAFFlogin.cloudflareaccess.orgFKBaalkLO7bp_y5_GhYtK8G1Pb_PlvTw84viVCRXP40QD
Select the domain you wish to attach the tunnel to.
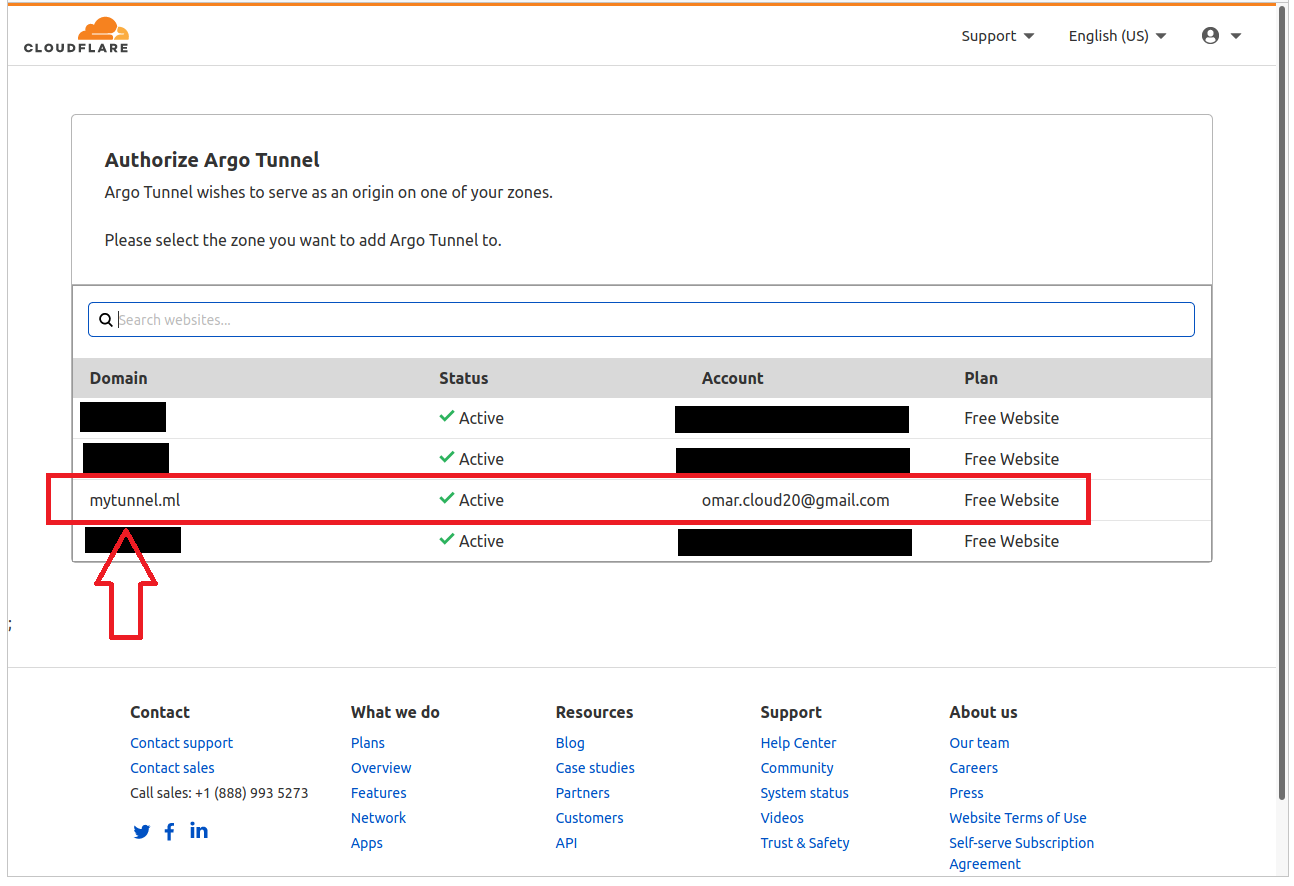
After which cloudflared confirms the certificate has been downloaded.
2. Getting the secret into Kubernetes
Store the cert.pem file as a secret in Kubernetes.
3. Deploying cloudlared into Kubernetes
As we are using Pulumi for our infrastructure as code solution we can show you how the deployment for cloudflared looks like in Typescript, which is pretty close to how the Kubernetes YAML would look.
The main thing to note is that you need to use a subdomain of your domain i.e. tunnel.yourddomain.com. After that if you want your root domain to point to the tunnel, you can use a CNAME in your domain setup.
4. Finally
You should now be able to access the web server in your cluster from tunnel.yourdomain.com.